Telecommunications services (Telco services) are critical infrastructure components for modern societies, supporting everything from voice communications to internet connectivity and cloud-based applications. As these services evolve to accommodate emerging technologies such as 5G, Internet of Things (IoT), and cloud computing, the security of telecommunications networks has become a paramount concern. This paper explores the process of securing Telco services, identifying potential threats, best practices, and strategic approaches to mitigating risks and enhancing overall security posture. By addressing both traditional and emerging security challenges, this paper provides a comprehensive framework for securing telecommunications services in an increasingly complex digital ecosystem.
Introduction
Telecommunications service providers (TSPs) face significant challenges in securing their networks and services due to the dynamic nature of the technologies involved and the growing sophistication of cyber threats. Telco services are integral to the global economy, enabling critical communication channels, financial transactions, healthcare systems, and more. As the reliance on these services increases, so too does the need for robust security measures to protect against a wide range of threats, including data breaches, DDoS attacks, insider threats, and vulnerabilities in both legacy and new technologies.
This paper outlines the process of securing Telco services, focusing on the identification of key risks, the adoption of best practices, and the integration of advanced security technologies into telecom infrastructures.
1. Threat Landscape for Telco Services
Telecommunications services are vulnerable to a broad array of security threats that can compromise the confidentiality, integrity, and availability of the services they provide. Some of the primary threats faced by TSPs include:
1.1. Cyberattacks
Telco services are common targets for cyberattacks such as Distributed Denial of Service (DDoS) attacks, man-in-the-middle attacks, and ransomware. These attacks can cause significant disruption to services, breach sensitive customer data, and degrade the quality of service. The increasing adoption of 5G and IoT technologies has amplified these risks, as more connected devices introduce new attack vectors.
1.2. Insider Threats
Given the sensitive nature of the data handled by TSPs, insider threats—whether from malicious or negligent employees—remain a significant concern. Insider threats can lead to unauthorized access to customer data, network manipulation, and disruption of services.
1.3. Supply Chain Risks
Telecom networks rely on third-party vendors for hardware, software, and services, making them vulnerable to supply chain attacks. These attacks can compromise network integrity, introduce vulnerabilities, and provide backdoor access to systems.
1.4. Vulnerabilities in Legacy Systems
Many telecom providers still rely on legacy systems that were not designed with modern cybersecurity threats in mind. These systems may contain unpatched vulnerabilities, outdated software, and weak access controls, making them an attractive target for attackers.
1.5. Privacy Concerns
As telecom companies handle vast amounts of personal and communication data, ensuring privacy and regulatory compliance (e.g., GDPR, CCPA) is a major concern. Data breaches could lead to regulatory fines, reputational damage, and loss of customer trust.
2. Securing Telco Services: Key Strategies and Elements to Include:
- User Devices: Endpoints that interact with the telco network (e.g., mobile phones, IoT devices, computers).
- Access Control Layer: Firewalls, VPNs, and identity management systems that control access to the network.
- Core Network: Centralized systems that provide essential telco services (e.g., voice, data, messaging).
- Cloud Infrastructure: External cloud resources that interact with the telco network.
- Security Operations Center (SOC): Centralized monitoring of network security events.
- Third-Party Integrations: External services (e.g., billing, customer management systems) that may have access to the telco infrastructure.
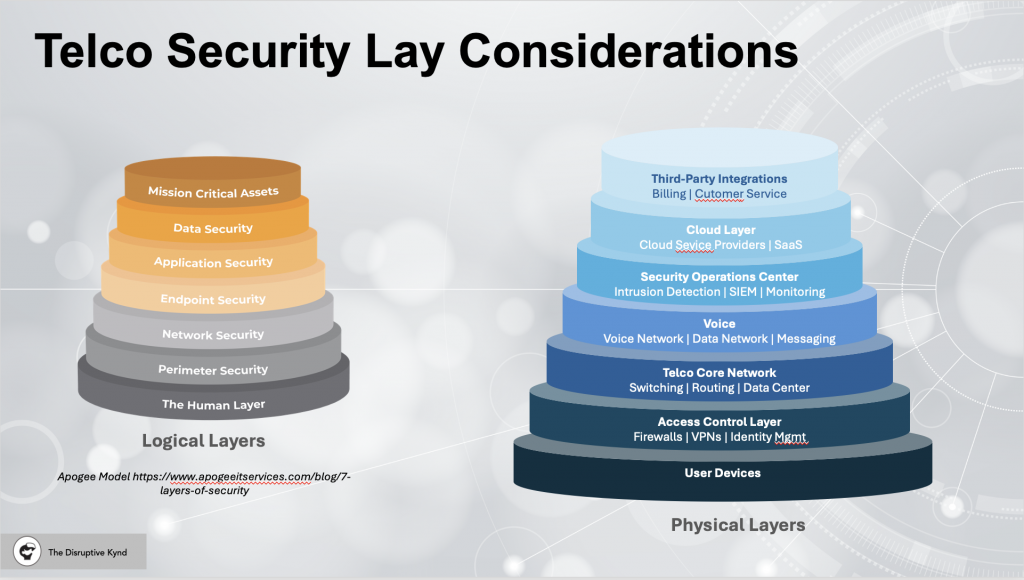
Securing Telco services requires a multi-layered approach that combines both traditional cybersecurity practices and advanced technologies. Below are the core strategies and best practices for securing telecom services:
2.1. Network Segmentation and Zero Trust Architecture
Network Segmentation: By segmenting telecom networks into smaller, isolated subnets, TSPs can reduce the attack surface and contain potential breaches within specific network segments. Segmentation ensures that even if one segment is compromised, the attacker does not gain access to the entire network.
Zero Trust Architecture: A Zero Trust approach assumes that no device, user, or application inside or outside the network is trustworthy by default. This model requires continuous verification of users, devices, and applications, using identity-based access controls, multi-factor authentication (MFA), and network monitoring to enforce security policies.
2.2. Robust Authentication and Access Control
Given the sensitive nature of telecom data, strong authentication mechanisms are essential. Best practices include:
- Multi-Factor Authentication (MFA): Implementing MFA for both internal employees and external customers ensures an additional layer of security.
- Role-Based Access Control (RBAC): Limiting access to sensitive information based on user roles helps ensure that only authorized personnel have access to critical systems.
- Least Privilege Principle: Users should only have access to the minimum resources required to perform their tasks.
2.3. Advanced Threat Detection and Monitoring
Real-time monitoring and threat detection are vital to identifying and responding to potential security incidents. Best practices include:
- Intrusion Detection Systems (IDS): IDS can detect unusual or suspicious traffic patterns, alerting security teams to potential attacks.
- Security Information and Event Management (SIEM): SIEM systems aggregate logs and security data from multiple sources to provide a centralized view of security events. Automated analysis can identify anomalies and trigger alerts.
- Artificial Intelligence and Machine Learning: Leveraging AI and ML algorithms can enhance threat detection by identifying patterns and anomalies in large volumes of network traffic and user behavior.
2.4. Encryption and Data Protection
Data confidentiality and integrity must be prioritized in telecom networks. Best practices for data protection include:
- End-to-End Encryption (E2EE): Encrypting data both at rest and in transit ensures that sensitive information is protected from unauthorized access.
- Public Key Infrastructure (PKI): PKI provides a secure method for encrypting communication and verifying the identities of devices and users in telecom networks.
- Data Masking and Tokenization: For sensitive data, using techniques like data masking and tokenization can prevent exposure in case of a breach.
2.5. Incident Response and Recovery Planning
Having a well-defined incident response plan (IRP) is essential for mitigating the impact of a security breach. Best practices include:
- Incident Response Team (IRT): Forming a dedicated IRT that is trained to handle a variety of cyber incidents, from DDoS attacks to data breaches.
- Regular Drills and Simulations: Conducting regular tabletop exercises and simulated attacks ensures that the IRT is prepared for real-world incidents.
- Business Continuity and Disaster Recovery: Telecom providers should implement disaster recovery plans that include data backups, redundant infrastructure, and failover capabilities to minimize service disruption in the event of a breach or system failure.
2.6. Supply Chain Security
Given the interdependencies between telecom companies and third-party vendors, securing the supply chain is essential. Best practices include:
- Vendor Risk Management: Establishing a formal risk management framework to assess and monitor the security posture of third-party vendors.
- Security Audits and Assessments: Conducting regular security audits of third-party vendors and requiring them to comply with the organization’s security policies and standards.
- Secure Development Lifecycle (SDLC): Ensuring that any software developed by third parties follows secure coding practices and undergoes regular security testing.
2.7. Regulatory Compliance and Privacy Considerations
Telecom companies must comply with various regulatory frameworks, such as GDPR, HIPAA, or CCPA, to ensure that they meet privacy and data protection requirements. Best practices include:
- Regular Audits and Reporting: Telecom providers should conduct regular audits to ensure compliance with applicable regulations and produce clear reports to demonstrate adherence.
- Data Minimization and Retention Policies: Implement policies to collect only the necessary data and retain it only for the required period, reducing exposure in case of a breach.
3. Emerging Technologies and Future Challenges
As telecom services evolve, new challenges and opportunities in cybersecurity will emerge. Key areas of concern include:
3.1. 5G Security
The rollout of 5G networks introduces new security challenges, particularly in relation to network slicing, edge computing, and the increased number of connected devices. Ensuring the security of 5G infrastructure requires robust authentication mechanisms, network isolation, and encryption protocols.
3.2. Internet of Things (IoT)
The proliferation of IoT devices in telecom networks increases the attack surface, requiring advanced device management, secure firmware updates, and real-time monitoring to detect and mitigate IoT-specific vulnerabilities.
3.3. Artificial Intelligence (AI) and Automation
AI and machine learning offer significant potential for enhancing network security by automating threat detection, response, and vulnerability management. However, these technologies also present new challenges, such as adversarial AI attacks and the need for robust explainability and transparency.
Conclusion
Securing Telco services is a multifaceted challenge that requires a combination of technological solutions, process improvements, and regulatory compliance. As telecom networks become more complex and interdependent, adopting best practices such as network segmentation, Zero Trust architectures, strong authentication, advanced threat monitoring, and incident response planning will be essential to protecting critical infrastructure. By proactively addressing security risks and leveraging emerging technologies, telecom providers can ensure the confidentiality, integrity, and availability of their services in an increasingly interconnected and digital world.
About the Author
Robert Erickson VP, Products, Strategy & Innovation
Entrepreneur | Sustained Growth Expert | Strategist | Mentor & Team Builder
Robert is seasoned high-tech software executive with more than 30 years of proven industry experience, both in entrepreneurial and enterprise corporate settings. With proven track record of bringing to market dozens of enterprise-class commercial platforms and products, Robert has built and led high-velocity product and strategy teams of product managers, developers, sales teams, marketing teams and delivery units.
His mission is to help enterprises achieve sustainable competitive growth through innovation, agility, and customer-centric value.
@Robert – www.linkedin/in/ericksonrw






Leave a Reply